Hello guys,
With the New Update from Aircrack-Suite, its now possible to use others system for the processing power.
(i know that CPU cracking is an old school technique but this tool is really fun :P)
with the new tool introduced in the aircrack suite, dcrack has the ability to perform Wireless Password Cracking in a Distributed Computing Environment. Isn't its COOL !! :D
ok then lets see how can we work on dcrack. (i just tired it now but i think its an AWESOME tool !! )
Note: I did not test this in a Fully Functioning Lab, I did the testing on VMware Workstation with 4 OS Running ( 1 User, 1 Server, 2 Clients).
STEP 1 - INSTALL AIRCRACK SUITE
Just refer to the aircrack website (http://www.aircrack-ng.org/install.html) for this.
STEP 2 - RUN DCRACK
To run dcrack, you need to know the working of dcrack.
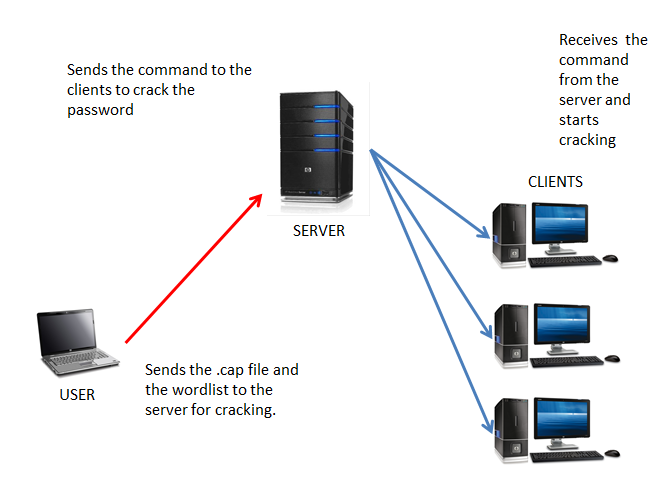
As we know now that dcrack utilizes the concept of Distributed Computing, so dcrack need three things :
A User
The User requests the server to crack the wireless password for him/her. The user will send the ".cap" file and a dictionary file (wordlist) to the server for cracking.
A Server
The server will be used as a Command Center. All the instructions, related to cracking will be given from here. The server will process the user's request for cracking and pass the instructions to the Clients.
Clients
Clients are responsible for do the dirty work !!
they use their processing power to crack the password using the wordlist given by the User.
To run dcrack, we need to go to the location where dcrack is located. so now in the terminal we'll go to :
/pentest/wireless/aircrack-ng/scripts/
First, the server needs to be start. Run the below given command to start the dcrack server.
python dcrack.py server
-------------------------------------------------
NOTE:
DCRACK SERVER IP : 192.168.1.128
CLIENT 1 IP: 192.168.1.131
CLIENT 2 IP: 192.168.1.133
USER IP : 192.168.1.132
MAC ADDR OF THE AP : 00:0d:93:eb:b0:8c
-----------------------------------------------------------
Second, the user needs to send the .cap file and the wordlist for the cracking to the server.
python dcrack.py cmd 192.168.1.128 cap /root/test.cap
python dcrack.py cmd 192.168.1.128 dict /root/password.lst
USER LOG ON SERVER (user sending the files to the server)
NOTE: The wordlist and the .cap file are compressed first to reduce the size to send it over the network.
Third, Both the clients (CLIENT 1 and CLIENT 2) needs to tell the server that its available for cracking.
python dcrack.py client 192.168.1.128
CLIENT 1
CLIENT 1 LOG ON SERVER
CLIENT 2
CLIENT 2 LOG ON SERVER
Now, the user needs to send the cracking request to the server
python dcrack.py cmd 192.168.1.128 crack 00:0d:93:eb:b0:8c
USER LOG ON SERVER
Once the user requests the server for cracking, the Clients will start downloading the wordlist and the .cap file from the server. Clients then uncompresses the files and then Splits the Wordlist in 2 parts (as we have 2 clients here) and then starts the cracking using their computing power.
CLIENT 1
CLIENT 2
CLIENT 1 LOG ON SERVER (Client sending the password to the server)
as you all can see above, CLIENT 1 found the key from the wordlist.
The user can check the status of the cracking using the below command :
python dcrack.py cmd 192.168.1.128 status
Phew !!
Too Long ... ha ha :D
That's all guys... i hope you like it.












